CVE-2024-9680
Mozilla Firefox Use-After-Free Vulnerability - [Actively Exploited]
Description
An attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild. This vulnerability affects Firefox < 131.0.2, Firefox ESR < 128.3.1, Firefox ESR < 115.16.1, Thunderbird < 131.0.1, Thunderbird < 128.3.1, and Thunderbird < 115.16.0.
INFO
Published Date :
Oct. 9, 2024, 1:15 p.m.
Last Modified :
Nov. 4, 2025, 2:35 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Mozilla Firefox and Firefox ESR contain a use-after-free vulnerability in Animation timelines that allows for code execution in the content process.
Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable.
Known Detected Feb 26, 2026
https://www.mozilla.org/en-US/security/advisories/mfsa2024-51/ ; https://nvd.nist.gov/vuln/detail/CVE-2024-9680
Affected Products
The following products are affected by CVE-2024-9680
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | CRITICAL | 134c704f-9b21-4f2e-91b3-4a467353bcc0 |
Solution
- Upgrade Firefox to version 131.0.2 or later.
- Upgrade Firefox ESR to version 128.3.1 or later.
- Upgrade Thunderbird to version 131.0.1 or later.
- Update affected packages based on vendor guidance.
Public PoC/Exploit Available at Github
CVE-2024-9680 has a 8 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2024-9680.
| URL | Resource |
|---|---|
| https://bugzilla.mozilla.org/show_bug.cgi?id=1923344 | Issue Tracking Permissions Required |
| https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 | Not Applicable Patch Vendor Advisory |
| https://www.mozilla.org/security/advisories/mfsa2024-51/ | Vendor Advisory |
| https://www.mozilla.org/security/advisories/mfsa2024-52/ | Vendor Advisory |
| https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=281992 | Issue Tracking |
| https://lists.debian.org/debian-lts-announce/2024/10/msg00005.html | Mailing List |
| https://lists.debian.org/debian-lts-announce/2024/10/msg00006.html | Mailing List |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-9680 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2024-9680 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2024-9680
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
Firefox/Tor Browser 0day exploit analysis (CVE-2024-9680) A UAF in animation timelines leading to RCE. Educational research. Patched.
0day exploit javascript tor patched html cve-2024-9680 browser-exploit firefox rce uaf use-after-free vulnerability
JavaScript HTML
A research-focused archive of publicly disclosed Windows zero-day vulnerabilities. This project summarizes CVEs, disclosure timelines, vendor advisories, and defensive mitigations. ⚠️ No exploit code included — educational and defensive use only.
cve cybersecurity infosec security-research threat-intelligence vulnerabilities windows zero-day
HTML
Queries, rules, and lab walkthroughs for threat hunting
None
Python
A bunch of V8 resources (with a security focus)
browser-exploitation v8
A vulnerability scanner for Firefox and Thunderbird that checks if your versions are out of date and susceptible to CVE-2024-9680.
Python
None
None
C HTML
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2024-9680 vulnerability anywhere in the article.

-
The Cyber Express
New Zero-Day in WinRAR Abused by RomCom
A new zero-day vulnerability in WinRAR (CVE-2025-8088) is being exploited in the wild by the Russia-aligned hacking group RomCom, according to newly published research from ESET. The flaw, silently ta ... Read more

-
The Register
Russia's RomCom among those exploiting a WinRAR 0-day in highly-targeted attacks
Russia-linked attackers found and exploited a high-severity WinRAR vulnerability before the maintainers of the Windows file archiver issued a fix. The bug, tracked as CVE-2025-8088, is a path-traversa ... Read more

-
BleepingComputer
Details emerge on WinRAR zero-day attacks that infected PCs with malware
Researchers have released a report detailing how a recent WinRAR path traversal vulnerability tracked as CVE-2025-8088 was exploited in zero-day attacks by the Russian 'RomCom' hacking group to drop d ... Read more

-
TheCyberThrone
Mozilla Firefox 139.0.4 Released
Mozilla has rolled out Firefox version 139.0.4 on June 10, 2025, as a part of its ongoing commitment to performance stability, user experience enhancement, and robust security. This is a point-release ... Read more

-
Daily CyberSecurity
Bridewell Uncovers ‘Operation Deceptive Prospect’ Targeting UK Organizations via Feedback Portals
Cyber threat actor RomCom—also tracked as Storm-0978, Tropical Scorpius, UNC2596, Void Rabisu, and UAC-0180—has launched a new cyber espionage campaign targeting UK-based retail, hospitality, and crit ... Read more

-
Cyber Security News
Google Warns of 75 Zero-Day Vulnerabilities Exploited in the Wild
Google’s Threat Intelligence Group (GTIG) has revealed that 75 zero-day vulnerabilities were exploited in the wild during 2024, highlighting both evolving attacker tactics and shifting targets in the ... Read more

-
The Hacker News
Google Reports 75 Zero-Days Exploited in 2024 — 44% Targeted Enterprise Security Products
Enterprise Security / Vulnerability Google has revealed that it observed 75 zero-day vulnerabilities exploited in the wild in 2024, down from 98 in 2023. Of the 75 zero-days, 44% of them targeted ente ... Read more
-
Google Cloud
Hello 0-Days, My Old Friend: A 2024 Zero-Day Exploitation Analysis
Written by: Casey Charrier, James Sadowski, Clement Lecigne, Vlad Stolyarov Executive Summary Google Threat Intelligence Group (GTIG) tracked 75 zero-day vulnerabilities exploited in the wild in 2024, ... Read more

-
BleepingComputer
Mozilla warns Windows users of critical Firefox sandbox escape flaw
Mozilla has released Firefox 136.0.4 to patch a critical security vulnerability that can let attackers escape the web browser's sandbox on Windows systems. Tracked as CVE-2025-2857, this flaw is descr ... Read more
-
Google Cloud
Cybercrime: A Multifaceted National Security Threat
Google Threat Intelligence Group Executive Summary Cybercrime makes up a majority of the malicious activity online and occupies the majority of defenders' resources. In 2024, Mandiant Consulting respo ... Read more

-
TheCyberThrone
Zeroday Vulnerabilities Prevailed in 2024 Analysis-Part II
This is the continuation of Zeroday vulnerabilities in 2024. Let’s delve deeply into the continuation of zero-day vulnerabilities of 2024, providing a comprehensive analysis.1. CVE-2023-46805: Authen ... Read more

-
europa.eu
Cyber Brief 24-12 - November 2024
Cyber Brief (November 2024)December 3, 2024 - Version: 1.0TLP:CLEARExecutive summaryWe analysed 232 open source reports for this Cyber Brief1.Relating to cyber policy and law enforcement, Germany anno ... Read more

-
The Hacker News
THN Recap: Top Cybersecurity Threats, Tools and Tips (Nov 25 - Dec 1)
Cyber Threats / Weekly Recap Ever wonder what happens in the digital world every time you blink? Here's something wild - hackers launch about 2,200 attacks every single day, which means someone's tryi ... Read more

-
The Register
Interpol nabs thousands, seizes millions in global cybercrime-busting op
Infosec in brief Interpol and its financial supporters in the South Korean government are back with another round of anti-cybercrime arrests via the fifth iteration of Operation HAECHI, this time nabb ... Read more

-
Help Net Security
Week in review: Exploitable flaws in corporate VPN clients, malware loader created with gaming engine
Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: Researchers reveal exploitable flaws in corporate VPN clients Researchers have discovered vulnerabilit ... Read more

-
SentinelOne
The Good, the Bad and the Ugly in Cybersecurity – Week 48
The Good | China Spy Handed 4-Year Jail Term Good news for national security this week as the U.S. Department of Justice successfully prosecuted a 59-year-old man for spying on behalf of China. Ping L ... Read more

-
Cybersecurity News
Zero-Day in Active Directory Certificate Services: Researcher Exposes CVE-2024-49019 with PoC
Security researchers from TrustedSec have uncovered a critical zero-day vulnerability, CVE-2024-49019, affecting Active Directory Certificate Services (AD CS). This flaw exploits a feature of version ... Read more

-
Hackread - Latest Cybersecurity, Tech, Crypto & Hacking News
Russian Hackers Exploit Firefox and Windows 0-Days to Deploy Backdoor
SUMMARY RomCom Exploits Double Zero-Day: RomCom, a Russia-linked group used previously unknown vulnerabilities in Firefox and Windows in a sophisticated attack campaign. Attack Chain: Visiting a malic ... Read more

-
The Cyber Express
Hackers Exploit Firefox and Windows Flaws: RomCom’s Advanced Attack Unveiled
A Russia-aligned hacking group, known as RomCom (also identified as Storm-0978, Tropical Scorpius, or UNC2596), has successfully exploited two zero-day vulnerabilities—one in Mozilla Firefox and anoth ... Read more
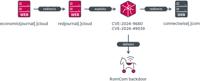
-
Cybersecurity News
RomCom Exploits Zero-Days in Firefox (CVE-2024-9680) & Windows (CVE-2024-49039) with No User Interaction
Exploit chain to compromise the victim | Image: ESETIn a recent cybersecurity report, ESET researchers have unveiled a coordinated attack by the Russia-aligned threat actor RomCom, exploiting zero-day ... Read more
The following table lists the changes that have been made to the
CVE-2024-9680 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Nov. 04, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-9680 Types: US Government Resource Added Reference Type CVE: https://lists.debian.org/debian-lts-announce/2024/10/msg00006.html Types: Mailing List -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 03, 2025
Action Type Old Value New Value Added Reference https://lists.debian.org/debian-lts-announce/2024/10/msg00006.html -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-9680 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-9680 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2024-9680 -
Modified Analysis by [email protected]
Nov. 26, 2024
Action Type Old Value New Value Added CPE Configuration OR *cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:* Changed Reference Type https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=281992 No Types Assigned https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=281992 Issue Tracking Changed Reference Type https://lists.debian.org/debian-lts-announce/2024/10/msg00005.html No Types Assigned https://lists.debian.org/debian-lts-announce/2024/10/msg00005.html Mailing List Changed Reference Type https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 Not Applicable https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 Not Applicable, Patch, Vendor Advisory -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference https://bugs.freebsd.org/bugzilla/show_bug.cgi?id=281992 Added Reference https://lists.debian.org/debian-lts-announce/2024/10/msg00005.html -
Modified Analysis by [email protected]
Nov. 19, 2024
Action Type Old Value New Value Changed Reference Type https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 No Types Assigned https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 Not Applicable Changed CPE Configuration OR *cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:* versions up to (excluding) 131.0.2 *cpe:2.3:a:mozilla:firefox_esr:*:*:*:*:*:*:*:* versions up to (excluding) 115.16.1 *cpe:2.3:a:mozilla:firefox_esr:*:*:*:*:*:*:*:* versions from (including) 128.0 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions up to (excluding) 115.16.0 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions from (including) 128.0.1 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:thunderbird:131.0:*:*:*:*:*:*:* OR *cpe:2.3:a:mozilla:firefox:*:*:*:*:esr:*:*:* versions up to (excluding) 115.16.1 *cpe:2.3:a:mozilla:firefox:*:*:*:*:esr:*:*:* versions from (including) 128.1.0 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:firefox:*:*:*:*:-:*:*:* versions up to (excluding) 131.0.2 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions up to (excluding) 115.16.0 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions from (including) 128.0.1 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:thunderbird:131.0:*:*:*:*:*:*:* -
CVE Modified by [email protected]
Nov. 18, 2024
Action Type Old Value New Value Added Reference Mozilla Corporation https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2024-49039 [No types assigned] -
Initial Analysis by [email protected]
Oct. 16, 2024
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H Changed Reference Type https://bugzilla.mozilla.org/show_bug.cgi?id=1923344 No Types Assigned https://bugzilla.mozilla.org/show_bug.cgi?id=1923344 Issue Tracking, Permissions Required Changed Reference Type https://www.mozilla.org/security/advisories/mfsa2024-51/ No Types Assigned https://www.mozilla.org/security/advisories/mfsa2024-51/ Vendor Advisory Changed Reference Type https://www.mozilla.org/security/advisories/mfsa2024-52/ No Types Assigned https://www.mozilla.org/security/advisories/mfsa2024-52/ Vendor Advisory Added CWE NIST CWE-416 Added CPE Configuration OR *cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:* versions up to (excluding) 131.0.2 *cpe:2.3:a:mozilla:firefox_esr:*:*:*:*:*:*:*:* versions up to (excluding) 115.16.1 *cpe:2.3:a:mozilla:firefox_esr:*:*:*:*:*:*:*:* versions from (including) 128.0 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions up to (excluding) 115.16.0 *cpe:2.3:a:mozilla:thunderbird:*:*:*:*:*:*:*:* versions from (including) 128.0.1 up to (excluding) 128.3.1 *cpe:2.3:a:mozilla:thunderbird:131.0:*:*:*:*:*:*:* -
CVE CISA KEV Update by 9119a7d8-5eab-497f-8521-727c672e3725
Oct. 16, 2024
Action Type Old Value New Value Added Due Date 2024-11-05 Added Date Added 2024-10-15 Added Vulnerability Name Mozilla Firefox Use-After-Free Vulnerability Added Required Action Apply mitigations per vendor instructions or discontinue use of the product if mitigations are unavailable. -
CVE Modified by [email protected]
Oct. 11, 2024
Action Type Old Value New Value Changed Description An attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild. This vulnerability affects Firefox < 131.0.2, Firefox ESR < 128.3.1, and Firefox ESR < 115.16.1. An attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild. This vulnerability affects Firefox < 131.0.2, Firefox ESR < 128.3.1, Firefox ESR < 115.16.1, Thunderbird < 131.0.1, Thunderbird < 128.3.1, and Thunderbird < 115.16.0. Added Reference Mozilla Corporation https://www.mozilla.org/security/advisories/mfsa2024-52/ [No types assigned] -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 09, 2024
Action Type Old Value New Value Added CWE CISA-ADP CWE-416 Added CVSS V3.1 CISA-ADP AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H -
CVE Received by [email protected]
Oct. 09, 2024
Action Type Old Value New Value Added Description An attacker was able to achieve code execution in the content process by exploiting a use-after-free in Animation timelines. We have had reports of this vulnerability being exploited in the wild. This vulnerability affects Firefox < 131.0.2, Firefox ESR < 128.3.1, and Firefox ESR < 115.16.1. Added Reference Mozilla Corporation https://bugzilla.mozilla.org/show_bug.cgi?id=1923344 [No types assigned] Added Reference Mozilla Corporation https://www.mozilla.org/security/advisories/mfsa2024-51/ [No types assigned]


